Index
- What is JWT?
- When to use and why?
- Application
𝗪𝗵𝗮𝘁 𝗶𝘀 𝗝𝗪𝗧?
Securing the API is one of the most important things to do to prevent its abuse. It is done via the authentication and authorisation process and the most used is the 𝗝𝗪𝗧 token-based mechanism.
JSON Web Token is a standard that is used to share information between client and server as a JSON object.
Official Introduction- https://jwt.io/introduction
It is represented as a string that consists of 3 parts: (Memory map JWT[3words 3 parts – H.P.S. – Header Payload Signature])
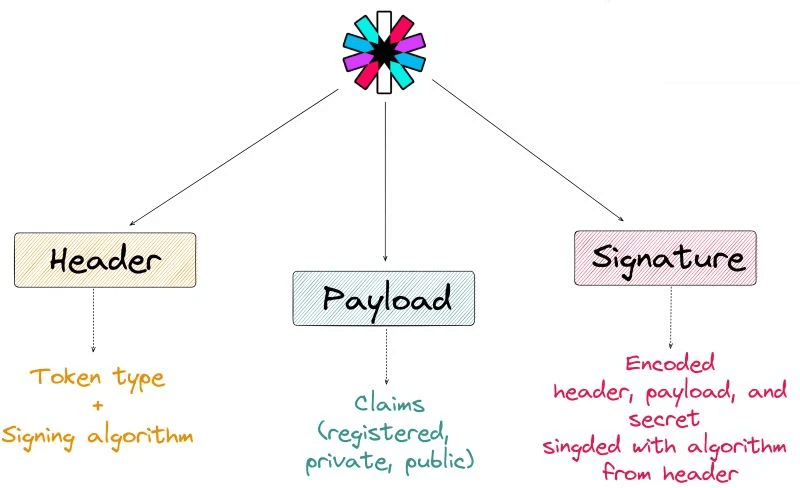
- 𝗛𝗲𝗮𝗱𝗲𝗿: It consists of token type(typ) and signing algorithm that is used(alg). The type will always be JWT, and the signing algorithm can be HMAC SHA256 or RSA.
- 𝗣𝗮𝘆𝗹𝗼𝗮𝗱: This part contains related data(mostly for users) known as claims. There are three types of claims:
- 𝗥𝗲𝗴𝗶𝘀𝘁𝗲𝗿𝗲𝗱 – claims that are recommended to use for interoperability like issuer(iss), subject(sub), expiration time(exp), etc.
- 𝗣𝘂𝗯𝗹𝗶𝗰 – contains generic information like email, name, or role. It’s recommended to use collision-resistant names to avoid collision with private claims.
- 𝗣𝗿𝗶𝘃𝗮𝘁𝗲 – custom claims
- 𝗦𝗶𝗴𝗻𝗮𝘁𝘂𝗿𝗲: It ensures that the token hasn’t been altered. JWT is signed with the algorithm from a header, and the signature consists of an encoded header and payload, and secret.
A string is always encoded like a Base64 string where every part is separated by dots and like that is easily passed in HTTP environments through HTTP headers.
Note:
- the claim names are only three characters long as JWT is meant to be compact.
- though signed tokens are protected against tampering, is readable by anyone(base-64 decry-pt). Do not put secret information in the payload or header elements of a JWT unless it is encrypted. (Note – the token is encoded not encrypted)
Relevant articles on encryption vs encoding
- https://www.geeksforgeeks.org/difference-between-encryption-and-encoding/
- https://auth0.com/blog/encoding-encryption-hashing/
Where JWT Is used? (refer official link above for description)
- Authorisation
- Information exchange
When to use and why?
In cases of S2S cases, no needed to maintain additional tokens for 3rd party.
Application